How much money would your business lose if a single email account were compromised? What about a single document? You would think that these actions are only a drop in the bucket of your business, but in reality, this is all it takes to cripple a company if the right access or data is stolen. Throughout the history of this blog, I have talked about the many different faces of phishing. Whether it be an email claiming to come from your boss, a potential customer, or even the government, all phishing emails have one thing in common, they are looking to steal something. This something is a big one. Who knows if they are looking for passwords to take over and compromise your accounts, or a wire transfer to a far away place never to be seen again? One malicious action that I have not yet touched upon is IP theft.
What is IP?
Intellectual property (henceforth referred to as IP) is defined as: A work or invention that is the result of creativity, such as a manuscript or a design, to which one has rights and for which one may apply for a patent, copyright, trademark, etc. IP can be anything from a logo design to an entire movie script and is material that can be protected under law through means such as a copyright. Unfortunately, this generally fails to deter malicious actors, and can cost the original artist, writer, etc. hundreds, and potentially millions of dollars. If the IP is not yet protected by a legal barrier, the malicious actor can sell, distribute, and profit off the stolen property with minimal or no legal repercussions. If they are in a country with less strict IP theft laws, a copyright might not even be enough to protect an artist’s hard work.
How does a malicious actor get access to IP?
Yet another form of phishing is involved in the theft, but this type is a bit more complex. Traditionally, phishing has some telltale signs that will allow users to identify and report it, and this is no different. The scam starts out as an email targeting a specific author, artist, or creator. In the example below, I am going to explain how a writer was targeted with the goal of access and distribution to a book not yet released.
It all starts with an official looking email with an ask to send the IP over. The message supposedly comes from a well-known company, but with a domain that looks a bit suspicious. The email also contains the spoof company’s logo, which cannot be shared as it is a protected image.

In this case, the email begins with a salutation and information that the authors new book has been approved for a movie deal. They then ask the target to send over the book’s manuscript along with a lot of other personal information.
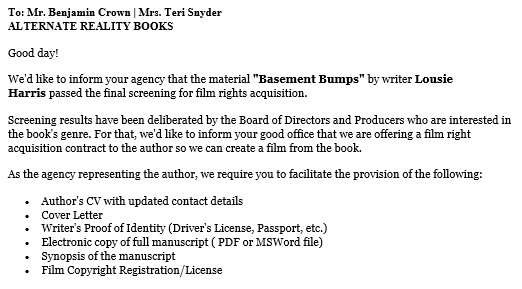
Additionally, all the legal jargon traditionally found in an offer letter is added to make the email sound more legitimate, and even includes the legal subtext that many companies use to protect sensitive information. All this information would be present in a real pre-production agreement email.

Lastly, the signature includes a name and email address with the same domain attached as the sender. They once again include the logo and this time a link to the official website. The link shown here is a link to the actual Universal Pictures website, but notice that the domain where the email is coming from as well as the ‘signoff’ email is just a bit different.
All in all, this is a meticulously thought out and well-designed email. If the author had not been aware of this type of phishing, the thought of a chance at stardom could blind anyone to the potential threat it contains.
How to prevent IP Theft?
There are a few different ways to protect against phishing, as well as protecting specific documents that contain sensitive or confidential information. I have written about Finchloom+ for Email Security in a few other blogs that can be found here, so I will not dwell on it too much. Those who have Finchloom+ for Email Security would have received a warning directly on the email above saying something along the lines of ‘Warning: This is the first time you received an email from this sender: submissions@universalpicturesacquisitions.com’. A chance to vet this email is a great start to securing any IP before it leaves the comfort of your hard drive, cloud storage, etc., and with Finchloom+ for Email Security, all it takes is a simple click of a button to have the email looked at first-hand by a security expert. Best case, the email is legitimate and returned to the authors inbox. Worst case, it is malicious, and the author is protected from the scam that they have been subject to. After vetting the initial email and once the attempt is deemed malicious, the domain is reported to the registrar and blocked from all company emails, as well as reported to the real company that they were trying to impersonate.

To protect employees, contractors, authors, and more from releasing their IP to the public, Finchloom+ for Email Security is a great start. Protecting the virtual documents on the other hand is just as critical. Microsoft offers tools to protect IP from getting into the wrong hands and has several different plans to enable user’s protection at every level.
Within Microsoft 365, there are several security and compliance measures that enable users to secure all different types of assets and information. In the case of a book/movie script, Information Protection is the specific tool that would aid authors and writers in protecting their IP. Information Protection ‘helps organizations discover, classify, label, and protect sensitive documents and emails. Admins can define rules and conditions to apply labels automatically, users can apply labels manually, or a combination of the two can be used—where users are given recommendations on applying labels.’ Depending on the label provided, a document can be open, password protected, or only provided to users with specific sign-in credentials. Going back to the example of IP theft, even if the author responded to the email, with the manuscript, the document would be protected as it would not be opened by a whitelisted email address with an approved sign-in, effectively stopping the theft without any additional work.
Similarly, if a malicious actor has access to a computer with sensitive data, they still need to log in to a Microsoft email, which, if set up with MFA, would be nearly impossible without the employee/target knowing as they would receive a notification on their secondary device. Information Protection is available in several Microsoft subscriptions including but not limited to Azure Information Protection Plan 1, Microsoft 365 F3/E3/E5, EMS (Enterprise Mobility & Security) F3/E3/E5, Microsoft 365 Business Premium – for businesses under 300 users, and Microsoft 365 F1/F3/E3/E5 to name a few. A la carte options are also available for some plans that do not already come with the service.
Compliance and Security solutions are the backbone of any business that is aware of the threats that face them. Before I worked at Finchloom, I never would have thought that manuscript theft was a commonplace issue, but here we are. I am looking forward to learning about the new threats that are realized throughout our future and seeing the technologies that are upgraded or created to fight them. In the case of IP theft as a broad term, Finchloom+ for Email Security and Microsoft are the dynamic duo that can win the fight against malicious actors targeting your company.
If you would like to learn more about Finchloom+ monthly managed services or the array of Microsoft security solutions that Finchloom offers, click here and fill out our form to speak with a security specialist. If you enjoy these blogs and would like to receive them weekly to your inbox, click here to subscribe! Thanks for reading!
